Secure and private messaging isn’t just for spies, whistleblowers, and revolutionaries. It’s an important and powerful tool that everyone should take advantage of. Why let anyone who wants to intercept your messages when you don’t have to?
It’s not about keeping your bank heist plans or world domination plot secret; it’s about making sure the things you write are only read by the people you want to read them. It doesn’t matter how mundane your texts are, it’s good practice to default to everything being super secure. That way, you don’t have to do anything special when you want to share a password, credit card number, or anything else sensitive through a text message.
5 things you should automate today
The good news is that sending secure, encrypted messages is as simple as sending unsecured, unencrypted messages. It’s just about using an encrypted message app that’s designed from the ground up to keep your communications private. I looked at over 20 different texting apps that purport to be secure and found three standouts that keep your secrets (and dinner plans) completely safe.
I’ve been writing about security for over a decade (and texting for a lot longer than that), and cybersecurity and encryption are part of my beat over at Popular Science. Most of all, though, I’m an expert in handing things off to more qualified experts. To assess the security of the different encrypted messaging apps, I didn’t just rely on my judgment. Instead, I used the assessments and opinions of security researchers and experts like Bruce Schneier and Brian Krebs. With that, here are our three favorite secure messaging apps.
The 3 best secure messaging apps
-
Signal for the best secure messaging app available
-
Session for the best totally anonymous messaging app
-
WhatsApp for the best secure messaging app that everyone uses
What makes the best secure messaging app?
The best encrypted messaging app is, first and foremost, actually secure. Everything else is kind of unimportant if criminals, governments, or tech company employees can potentially access your messages, whether it’s through hacks, the legal system, or admin tools. No amount of promises that your data won’t be used or can’t be accessed is enough to overcome the fact that if it is at all possible, people will do it.
The gold standard in secure communications is end-to-end encryption. This means that from the moment your message leaves your phone until it reaches your recipient, it’s just strings of unintelligible data. It doesn’t matter if someone gets access to your “message” while it’s in transit—without the encryption key that only your intended recipient has, it can’t be read. Even the tech company operating the whole system can’t see the contents of your messages.
The underlying principle that enables end-to-end encryption is called public-key cryptography, and how it works is incredibly cool. To oversimplify things dramatically, every user has a pair of keys: a public key and a private key. Everyone can see someone’s public key, but the private key is a total secret. To send someone an encrypted message, you encode it using their public key. To read it, they use the matching private key to unlock the message. Because of the math involved, the public key can’t be used to decode it, which is why the system is so effective. (In reality, the most secure apps now use keys that regularly change, so even if someone intercepts one message, they can’t read future messages.)
There are a couple of important related features that go with end-to-end encryption. On the most secure messaging app, you can verify that you’re talking to the person you think you are, data is stored encrypted on your device, and you can reset your encryption keys at any time. When putting together this list, I was looking for a complete implementation of end-to-end encryption best practices.
Another important aspect of a secure texting app is that it’s open about how everything is encrypted—and it’s all been verified. Using powerful algorithms properly is much more effective than trying to prevent bad actors from finding out how an app works (a technique called “security through obscurity“). Most of the best secure apps are open source, which means that anyone who wants to can look at the code on GitHub and check that it does what the developers say it does. Another option here is that the app has been audited by reputable third-party security companies, although that’s not as preferable.
Beyond secure text messaging, there were a few other factors I was looking for:
-
As little history of privacy violations from the developers as possible. While bad people can build good apps, it’s best if the interests of the users line up with the stated and demonstrated positions of the developers where security is concerned.
-
Nice to use. There are quite a few encrypted messaging apps available, so if you’re looking for the best, you want one that’s actually nice to use. All our picks are great texting apps—they also just happen to be super secure.
-
Free (or at least cheap). Because of the political nature of messaging, many secure apps are built by non-profit foundations and activist-developers. It’s great for us because you don’t have to spend a fortune to get high-grade encryption. All the apps on this list are free.
I considered and tested more than 20 different secure texting apps. The most important part was verifying that they were always secure and had no unfixed problems. This eliminated about half the apps from the list, as they either weren’t end-to-end encrypted or only were under specific circumstances. For the 10 or so apps that met my security criteria, I dug a bit deeper and used them for a few days to see how they worked. I do a lot of texting, so it was pretty easy to get a feel for whether the apps were a worthy SMS or Facebook Messenger replacement.
And that was enough to cut the list down to just three great secure picks.
The best secure messaging app
Signal
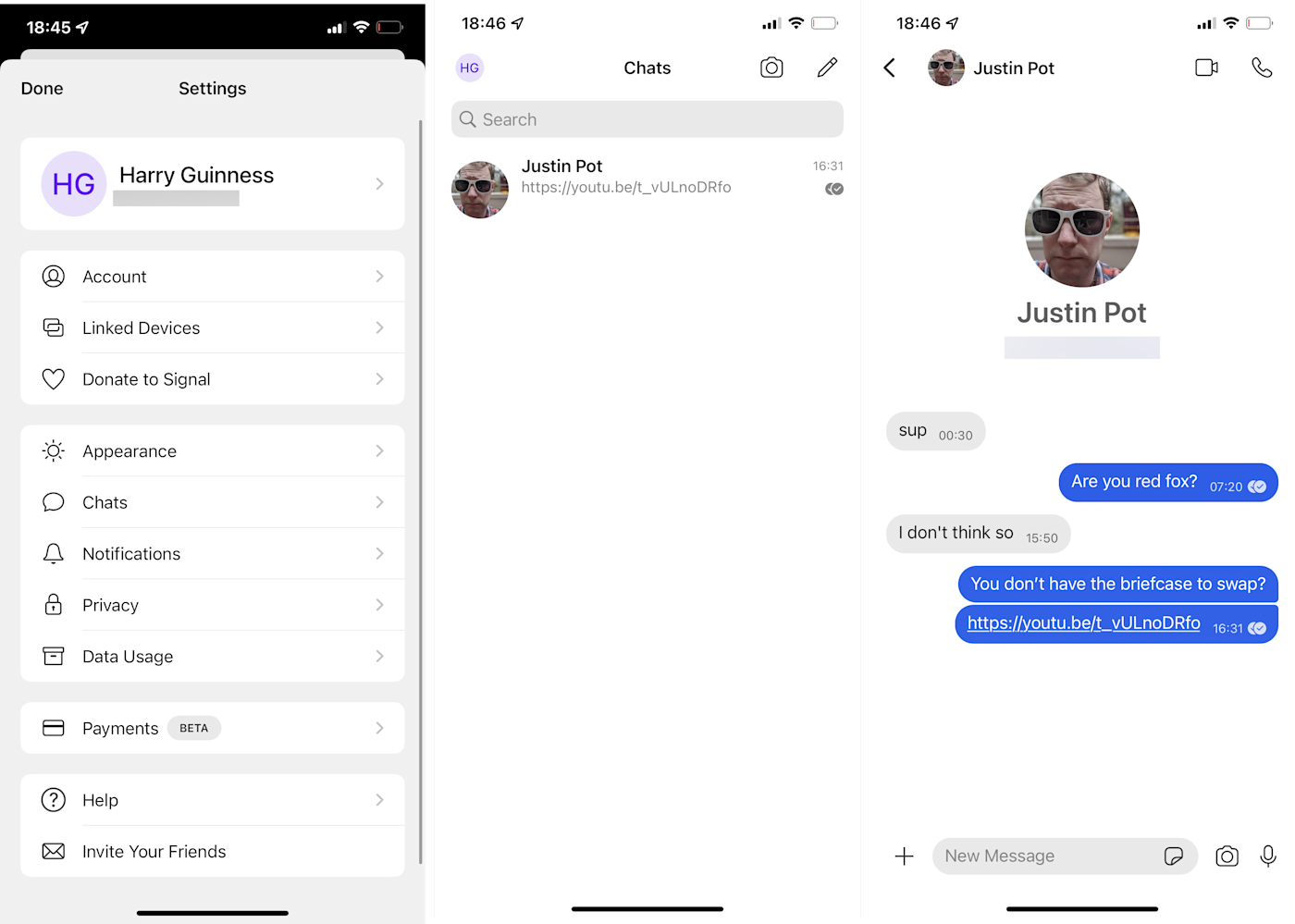
Signal is the benchmark secure text messaging app—it’s the one that almost all the security professionals recommend. It’s openly and unapologetically trying to keep conversations private, whether they’re about the weather or resisting an authoritarian government. Crucially, Signal is run by the non-profit Signal Technology Foundation. It’s entirely funded by donations, so there are no ads, trackers, or other privacy-sacrifices made in the name of monetization.
Signal developed and uses the open source Signal Protocol to encrypt everything. It’s peer-reviewed, fast and effective, and, you guessed it, incredibly secure. It’s such a good end-to-end encryption implementation that apps from major tech companies, like WhatsApp and Google Messages, use it for their encrypted messages.
Aside from being the most widely respected secure messaging app, Signal is just the complete communication package. You can send text messages, pictures, videos, files, voice notes, stickers, and everything else you’d expect to individual contacts or chat groups. You can make end-to-end encrypted voice and video calls with up to 40 people at once. Really, the only negative is that the app lacks a bit of personality and customization. It’s clean and minimal, but other messaging apps feel a bit more fun.
Signal is exploding in popularity at the moment, so there’s a good chance some of your contacts already use it. If not, it’s a pretty easy sell. It’s free and as good as any non-secure option.
Signal pricing: Free
The best anonymous messaging app
Session
Signal stores as little metadata about you as possible. But because your account is tied to a phone number, there’s a tenuous connection. We highly doubt Signal would ever reveal this information willingly, but at least theoretically, an authoritarian government could get a list of every phone number with a Signal account, cross-check it with cell phone companies, and arrest everyone with Signal as a dissident. Far-fetched? Absolutely, but this is the kind of attack vector that security researchers consider.
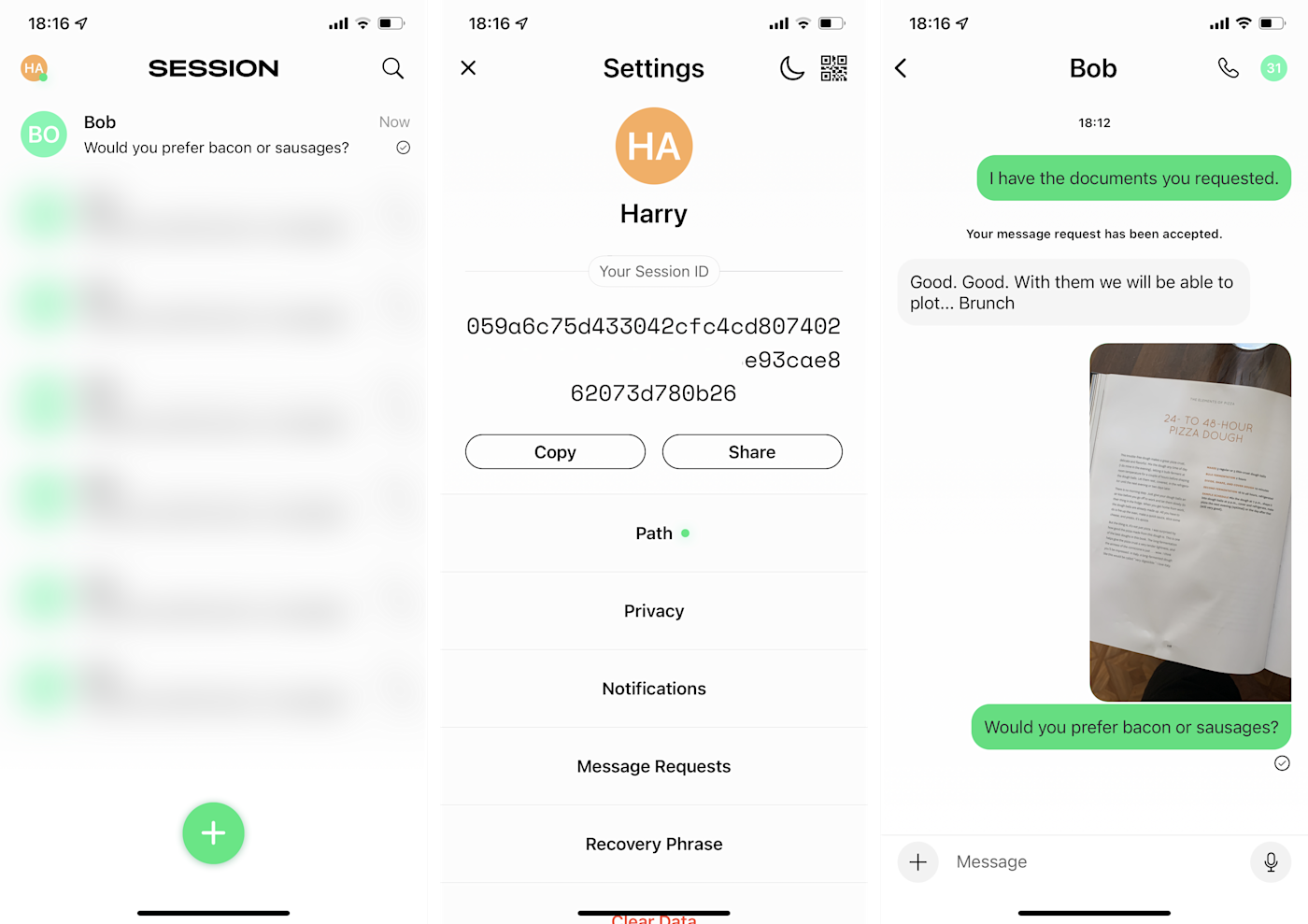
Session—which started life as a “fork” of Signal’s codebase—solves this problem by not requiring a phone number or email address when you sign up. Your account is simply a long string called a Session ID. To start a conversation with someone, you tap Start a Session and then either scan a QR code or enter your recipient’s session ID. After that, it’s a normal messaging app. You can send texts, photos, files, and even voice notes. The developers are working on encrypted phone calls, but it’s only available as a beta at the moment.
To log in to your Session account (not that it’s really an account), you need a long recovery phrase—the one assigned to me has 13 words in it. It’s a clever system, as it means you can keep your Session ID active and move between devices, without Session needing to verify a phone number, email address, or anything else identifying.
Session is designed to collect as little metadata as possible. The app doesn’t track your IP address, device details, location, or anything else. While Signal uses central servers, Session is entirely decentralized. Your encrypted messages are sent using an “onion network,” which routes requests through different servers to hide your IP address. While in transit, your messages are stored on a “swarm” of nodes. They’re deleted as soon as you receive them. All in all, this makes Session use incredibly anonymous and deniable. There’s no way to tie a particular person to a particular account without having physical access to their device (in which case, you probably have bigger problems).
The biggest downside of Session is that it’s not as nice or feature-filled as Signal. If you don’t need the total anonymity, it’s harder to recommend. Also, it’s developed in Australia, where the government has historically been anti-encryption. Session’s cryptographic bonafides are solid, but if the government came knocking, the developers could theoretically be forced to weaken their app’s security. How they would be able to hide that in an open source codebase would remain to be seen, but again, the point with these kinds of thought experiments is to flag the edge cases.
Session is great and almost certainly safe and anonymous, but it’s important to understand where it could fall short if you’re going to use it to make brunch plans.
Session pricing: Free
The best secure messaging app that people already use
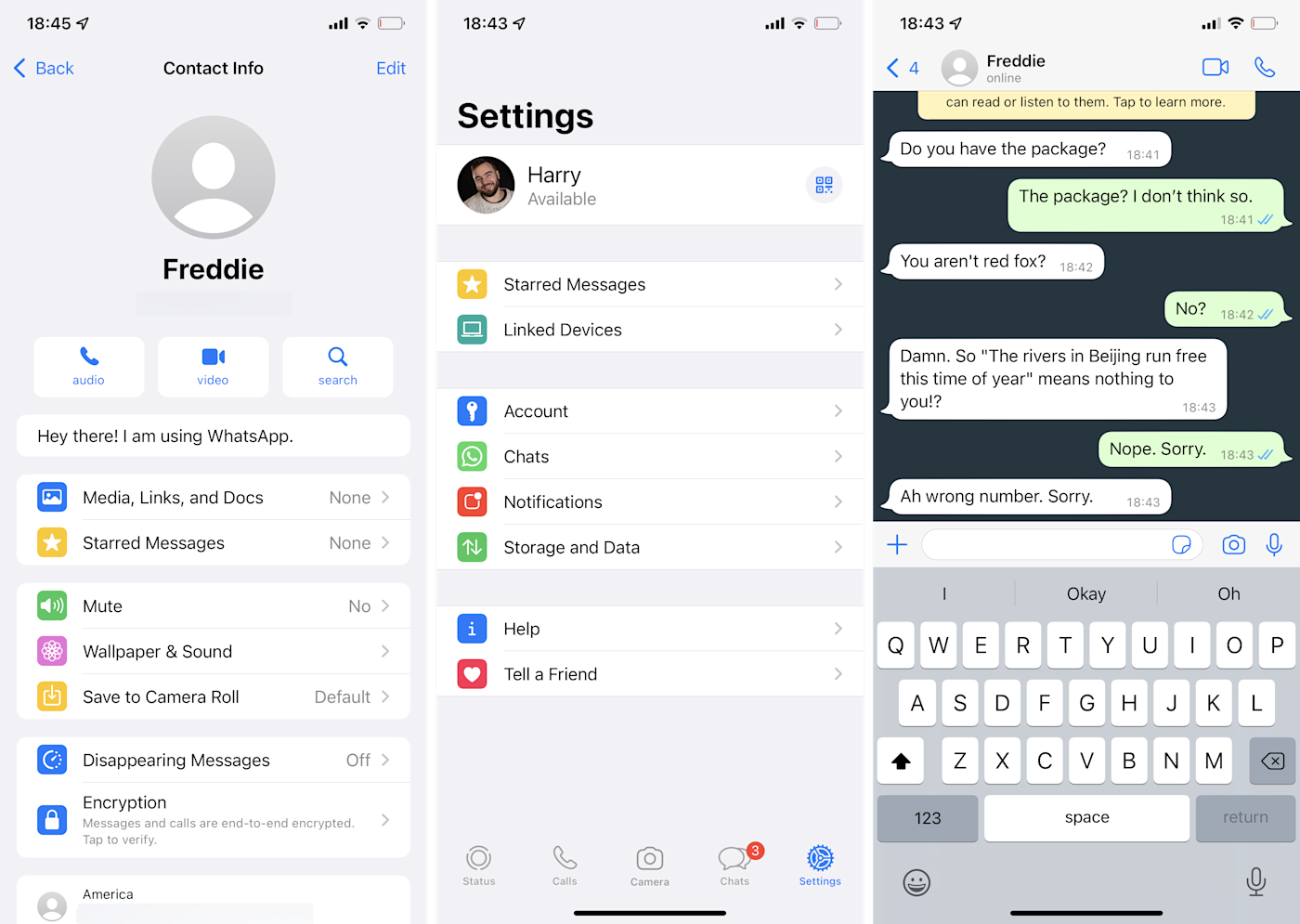
WhatsApp, with more than two billion active users around the world, is by far the most widely used end-to-end encrypted messaging app. It’s great to use, and all your text messages, pictures, voice messages, phone and video calls, files, and everything else you send are encrypted using the Signal Protocol between you and your recipient’s devices.
Or they’re meant to be.
WhatsApp is genuinely built to be a secure, encrypted communication platform. Its security audits and technical explanations check out. It uses one of the best encryption protocols available. It’s the real deal. The problem is that it’s owned by Meta (formerly known as Facebook), which doesn’t have a great history of protecting and respecting privacy.
Leaving aside the various scandals around Facebook and Facebook Messenger (which isn’t encrypted from end-to-end), Meta employees read private WhatsApp messages when users are reported, and the company has cooperated with and turned information over to prosecutors. It also collects a lot of metadata, like who you talk to, how often, and from where. It’s a lot more metadata than Signal stores, though exactly how much more isn’t public knowledge. It is still a bit troubling, as it can be used to reveal or construe information you might want to keep private.
With all that said, WhatsApp still makes our list of the best secure messaging apps for a few reasons. First, these situations are the extreme outliers. If your recipients aren’t reporting your messages, they can’t be read by anyone at Meta. That means it’s still significantly more secure than messaging apps that don’t use end-to-end encryption and in an entirely different league than SMS. It’s also wildly popular, so there’s a good chance your contacts are already using it. If you can’t convince them to switch to Signal, using WhatsApp is the next best thing.
There are also some parts of the world and situations where having Signal installed on your smartphone could be interpreted as a suspicious activity in and of itself. WhatsApp, however, is used by a significant chunk of the world’s population. If you’re traveling somewhere, and you’re concerned about how authorities there will feel about your encrypted messaging app, go with WhatsApp.
With that out of the way, it’s worth noting that WhatsApp is near the top of our favorite texting apps for a reason. It is far and away Meta’s best product—and one I use daily.
WhatsApp pricing: Free
Why some messaging apps didn’t make this list
Signal is the clear pick if you’re looking for the best encrypted messaging app; Session is useful if you want more anonymity; and WhatsApp is secure enough for daily use for most people and justifiably popular. But there are a few apps you might have expected to see on this list, so I wanted to run through some of the reasons they were excluded.
-
iMessage. Apple’s iMessage is end-to-end encrypted, but it’s not available on all mobile platforms. Also, I didn’t love that encrypted iMessages and entirely unencrypted SMS messages are sent from the same app (and, if an iMessage fails to send, it can automatically be resent as an SMS). If you use it, your data is almost certainly safe, but these small issues were enough to keep it from the list.
-
Telegram. Telegram doesn’t use end-to-end encryption by default. It claims its MTProto Mobile Protocol is sufficient, but enough security experts and researchers have issues that I couldn’t fully recommend it.
-
Facebook Messenger. Messenger doesn’t use end-to-end encryption by default. Don’t use it if you’re security-conscious.
-
Google’s various messaging options. Google’s different messaging services—Duo, Meet, Chat, and Messages—support different levels of encryption. The generally poor user experience (and Google’s failure to settle on one messaging platform) was enough to keep them from the list.
-
SMS. SMS is a terrible, dated protocol. It’s vulnerable to a variety of different hacks and scams. It’s possible for bad actors to call your carrier, impersonate you, and have all your incoming messages (including 2FA tokens) forwarded to a new SIM card.
[adsanity_group align=’alignnone’ num_ads=1 num_columns=1 group_ids=’15192′]
Need Any Technology Assistance? Call Pursho @ 0731-6725516




